Cyber Security - the human being as a risk factor
The danger of being subject to a cybercrime attack affects companies and organisations of all sizes and industries. Ex-FBI Director Robert Mueller's statement fits this very well" There are only two types of companies: Those that have been hacked and those that will be." The recent large-scale attack by the hacker group "REvil" on the IT service provider Kaseya has once again shown the dangerous dimension that such cybercrime attacks can have. In this case, about 1500 companies were damaged by having their data encrypted.
Humans are the main risk in cyber security, because the most frequent mistakes are made by humans, e.g. by opening an email with an infected attachment or link, which infects the company's IT. Here, it is important to implement various measures as a precaution (see Handelsblatt, "Hacker nutzen den Risikofaktor Mensch", Lars-Marten Nagel, 7 July, 2021, No. 128). This includes training for the entire staff so that they act more cautiously and recognise such dangers better. On the other hand, various technical mechanisms must be introduced and especially also permanently checked and updated in order to have a chance of not being constantly infected with the constantly changing attack variants.
Backup is one of the key elements for IT security and availability. Firstly, the solution itself is crucial in that it can comprehensively secure the entire IT environment and has appropriate security elements so that corruption is very difficult. With SEP, the entire IT environment can be secured, including cloud applications such as Microsoft 365, Dynamics 365, Salesforce and Google Workspace.
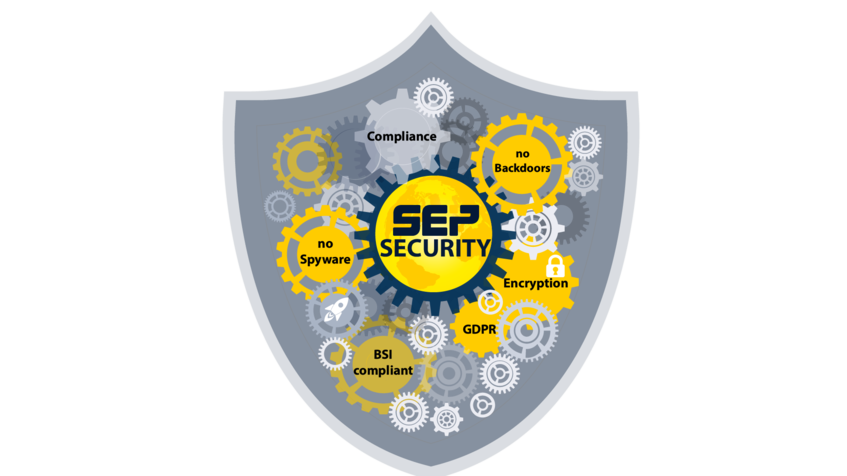
As a German/European manufacturer, SEP guarantees freedom from backdoors - i.e. no pre-programmed vulnerabilities/backdoors!
SEP also guarantees the "No-Spy Clause" of the BMI - the Federal Government Commissioner for Information Technology in coordination with the IT association Bitkom, i.e. "...that the standard software* to be supplied by it is free of functions that endanger the integrity, confidentiality and availability of the standard software*, other software and/or hardware or data and run counter to the confidentiality or security interests of the customer through
- Functions for the undesired discontinuation/derivation of data,
- Functions for undesired modification/manipulation of data or flow logic, or
- Functions for the undesired initiation of data or undesired function extensions." (Clause 2.3 of the EVB-IT Überlassung Typ A-AGB; Supplementary Terms of Contract for the Procurement of IT Services (EVB-IT); Special Terms of Contract for the Procurement of IT Systems and Equipment (BVB) )
GDPR and compliance requirements: the hybrid backup solution SEP sesam offers the technical security for implementing the GDPR with a variety of technical mechanisms (see " EU General Data Protection Regulation, EU NIS Directive & IT Security Act“, lawyer and IT law specialist Dr. Jens Bücking, p. 11 ff; www.sep.de/fileadmin/user_upload/Compliance/SEPsesam_Compliance_EN_web.pdf)
Backup concept and continuous review: In addition to the selection of the backup software, it is particularly crucial that the requirements are carefully reviewed and the backup concept is precisely aligned with them. SLAs must be defined so that in the event of an error, cyber attack, etc., the data can be brought back according to the specified SLAs and a fast restart is guaranteed and the recovery points (RPOs) have been planned in a correspondingly granular manner. The use of the backup media must also be taken into account, because for short SLAs, higher-performance media are needed so that the recovery time objective (RTO) fits.
A multi-level backup is also recommended, e.g. 3-2-1 rule, so that the data is stored on different media, in different locations and ideally also offline. This makes it even more difficult to access the backup data in the event of a cyber attack.
Constant monitoring and adjustment: Regular recovery tests are essential so that you are prepared in case of an emergency and know what to do, because only what has been practised often can be called up well under stress - even the fire brigade trains regularly. In addition, such tests also reveal weak points, so that adjustments can and must be made. Cyber criminals also change their methods of attack and therefore one's own IT environment and security mechanisms must always be kept up to date.
Andreas Mayer
Back